Intelligent Honeypot for the Internet of Things

A virtual PBX that analyzes suspicious traffic, identifies attackers, and tries to predict their fraudulent behavior. PBXs in operation tend to be connected to the Internet and therefore vulnerable to cyber-attacks and misuse. We deploy Honeypot to protect you from such attacks.
The product is situated in industrial and service networks, where the detection of unwanted behaviour has not been very common so far. As these networks are becoming more and more connected to the Internet, it is necessary to monitor malicious traffic as well. A honeypot is essentially a special probe that enables this monitoring.
What problems does it solve for its customers?
The deployment of the demonstrator is directed towards the rapidly developing segment of cyber protection of operational systems, the so-called OT environment (operational technology), where these elements have been deployed very sporadically and, in comparison to classic IT, require some adaptation to the specifics of the environment. The customer thus has a platform demonstrator that can be adapted to different deployment segments.
One possible application is in the market for Internet telephony providers (using the VOIP family of protocols). Operators have PBXs that are connected to the Internet and are therefore vulnerable to cyber-attacks and misuse. Our solution inserts a virtual PBX into their network, which behaves like a traditional PBX (connecting subscribers, routing calls) but also analyzes suspicious traffic, identifies attackers and tries to predict their fraudulent behavior.
Product development phase
A demonstrator is currently available for customers that can be adapted to different deployment segments. One possible application is in the market for Internet telephony providers (using the VOIP protocol family).
With our system it is possible to minimize the losses incurred by providers of these telephone services. Compared to other solutions, our solution is difficult to detect as a "trap" from the attacker's point of view. This is because the attacker is not able to recognize that it is a security measure, increasing the time to react and take appropriate measures. Our demonstrator is ready for this segment at TRL 4 technology readiness level.
Commercialisation method
Collaboration agreement/work agreement/ + NDA can be signed with interested parties. Alternatively, negotiations can be initiated with companies for collaboration in the form of a joint research project or sponsored research in this area. This will ensure the development of existing know-how and enable longer term development of knowledge capacity in this segment, through building scientific capacity on cyber security.
Technical specifications
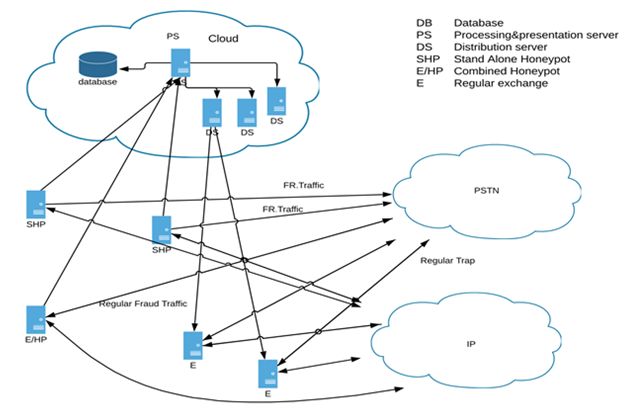
The SIP attack traffic analysis environment ("SIP honeypot") is an integrated set of several subsystems and tools, designed for monitoring attacks on VoIP/SIP infrastructure in the enterprise, in the environment of IP voice service providers, in the educational sphere, but also in a simple deployment for any interested IP telephony enthusiast.
The demonstrator contains a network of conventional and intelligent honeypots, among which the distribution server distributes incoming traffic from the VOIP PBX. In this traffic, the system searches for anomalies that indicate a potential attacker (defrauder). The system then tests the response of conventional honeypots that are currently available and compares them with the responses implemented by our proposed "intelligent" honeypots. The behavior of the attacker and their forensic identification (fingerprint) are then transmitted to the server part, which processes them and provides information for later analysis and for the subsequent selection of actions that the intelligent honeypot then implements depending on the behavior of the attacker.
The aim is both high resolution (identification) of attackers according to specific behavioural characteristics and consequently high defensiveness of the control panels connected to our server, all with the aim of minimising financial loss.

Are you interested in this technology?
If you are interested in our technology, products and services, please contact our Technology Transfer Coordinator by phone or email:

